FAQ
Q:
Where are test vectors?
A:
https://github.com/BLAKE2/BLAKE2/tree/master/testvectors
Q:
How can I be sure the BLAKE2 is secure?
A:
We have no proof that BLAKE2 is as secure as we claim, but there are
good reasons to believe it:
BLAKE2 relies on (essentially) the same core algorithm as BLAKE, which
has been intensively analyzed since 2008 within the SHA-3 competition,
and which was one of the 5 finalists.
NIST's final
report writes that BLAKE has a "very large security margin", and
that the the cryptanalysis performed on it has "a great deal of
depth".
The best academic attack on BLAKE (and BLAKE2) works on a reduced
version with 2.5 rounds, whereas BLAKE2b does 12 rounds, and BLAKE2s
does 10 rounds.
But even this attack is not practical: it only shows for example that
with 2.5 rounds, the preimage security of BLAKE2b is downgraded from 512
bits to 481 bits, or that the collision security of BLAKE2s is
downgraded from 128 bits to 112 bits (which is similar to the security
of 2048-bit RSA).
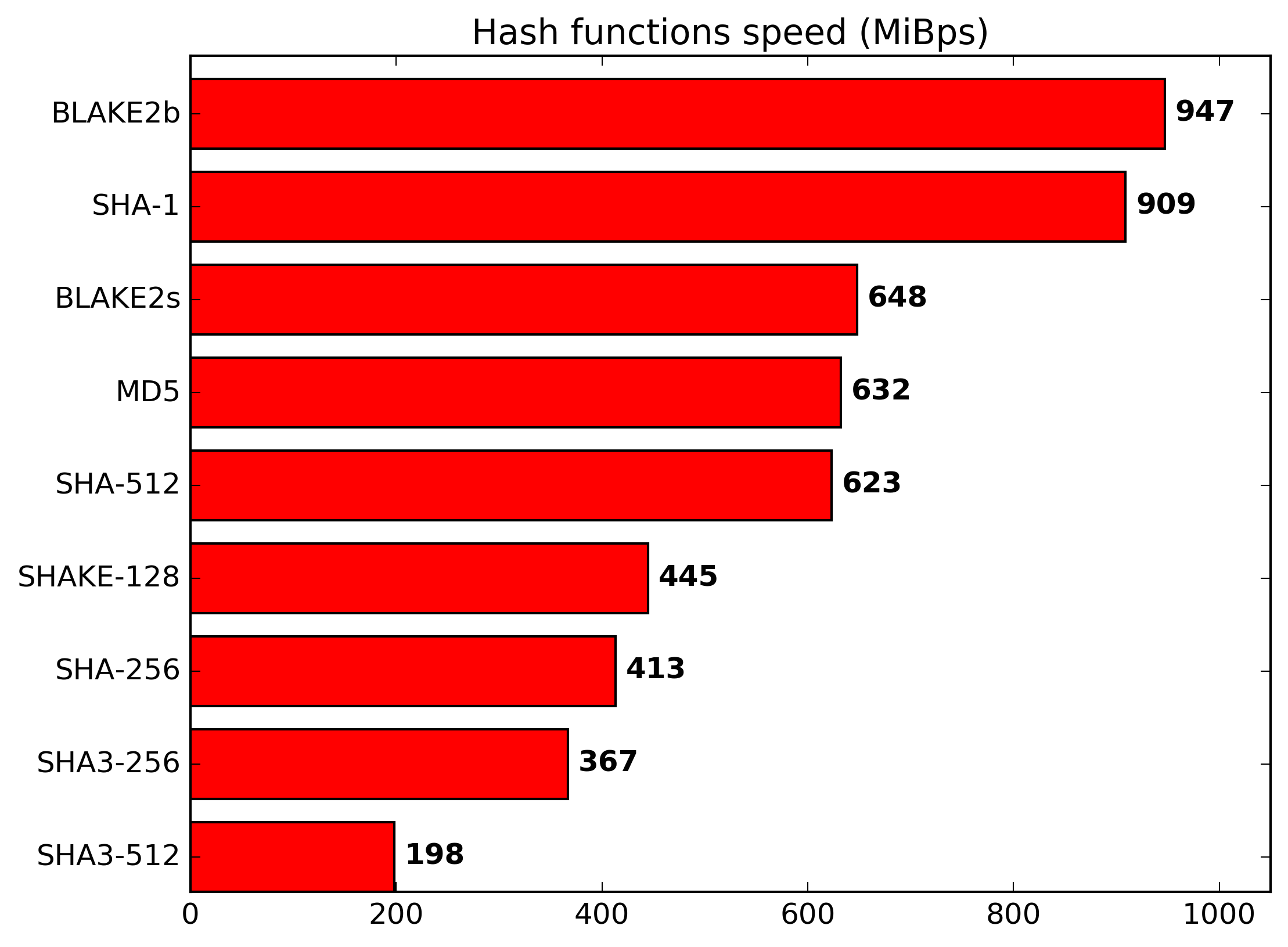
Q:
Why is BLAKE2 so fast?
A:
BLAKE2 is fast in software because it exploits features of modern CPUs,
namely instruction-level parallelism, SIMD instruction set extensions,
and multiple cores.
BLAKE2 also benefits from the optimization work performed during the
SHA-3 competition (see for example this paper by two of
the designers of BLAKE2).
Q:
Why do you want BLAKE2 to be fast? Aren't fast hashes bad?
A:
You want your hash function to be fast if you are using it to compute the
secure hash of a large amount of data, such as in distributed filesystems (e.g.
Tahoe-LAFS), cloud storage systems (e.g. OpenStack Swift), intrusion detection
systems (e.g. Samhain), integrity-checking local filesystems (e.g. ZFS),
peer-to-peer file-sharing tools (e.g. BitTorrent), or version control
systems (e.g. git).
You only want your hash function to be slow if you're using it to
"stretch" user-supplied passwords, in which case see the next question.
Q:
So I shouldn't use BLAKE2 for hashing user passwords?
A:
You shouldn't use *any* general-purpose hash function for user
passwords, not BLAKE2, and not MD5, SHA-1, SHA-256, or SHA-3.
Instead you should use a password hashing function such as the PHC winner
Argon2 with
appropriate time and memory cost parameters, to
mitigate the risk of bruteforce attacks—Argon2's core uses a
variant of BLAKE2's permutation.
Q:
BLAKE2bp gives different results from BLAKE2b. Is that normal?
A:
Yes.
BLAKE2bp is a different algorithm from BLAKE2b and BLAKE2sp is a
different algorithm from BLAKE2s.
Each algorithm produces a different hash value.
BLAKE2b and BLAKE2s are designed to be efficient on a single CPU core
(BLAKE2b is more efficient on 64-bit CPUs and BLAKE2s is more efficient on
8-bit, 16-bit, or 32-bit CPUs).
BLAKE2bp and BLAKE2sp are designed to be efficient on multicore or SIMD
chips, by processing the input in parallel.
This parallel approach results in different secure hash values from the
single-core variants.
More generally, two instances of BLAKE2b or BLAKE2s with two distinct
sets of parameters will produce different results.
For example, BLAKE2b in some tree mode (say, with fanout 2) will produce
different results than BLAKE2b in a modified tree mode (say, with fanout
3).
Q:
Which should I use? BLAKE2b, BLAKE2s, BLAKE2bp, or BLAKE2sp?
A:
A rule of thumb is that on 64-bit platforms the best choice is BLAKE2b,
whereas on 32-bit (or smaller) platforms BLAKE2s is recommended.
Or, you could try each of the four of them and see which one
performs best on your deployment platform.
If you do that, please write to us and let us know what you found.
Q:
The BLAKE2 documentation only describes differences with the original
BLAKE, where can I find a complete specification?
A:
The RFC includes a
complete specification of BLAKE2b and BLAKE2s (though not of the tree
mode).